Understand the Most Common Compliance Rule Violations
Learn how to protect your organization from it
Data breaches, security concerns, and regulatory fines all stem from a common cause: ignoring company compliance rules.
One striking case of compliance rule violations involved Uber in the Netherlands, where Uber faced a fine of 290 million euros for failing to protect sensitive personal information of their drivers.
Not only were Uber’s security and access controls lacking, but they transferred the data from Europe to the US without using the legally required data transfer tools (e.g. SCCs).
This is not only a massive fine, but such compliance rule violations reduce user trust and cause considerable damage to the company's image.
Right now, many organizations are asking themselves: "Are my compliance rules working?" In this blog, we will discuss the most common compliance flaws and introduce SpaceObServer as a solution to address them.
Where companies often fail compliance
While not every case is as severe as the Uber case, the reality is that most organizations face more subtle but recurring issues in their daily operations.
Uber’s case showed a systematic failure to secure international data transfers, whereas in many other organizations violations are more often the result of misunderstanding or oversight.
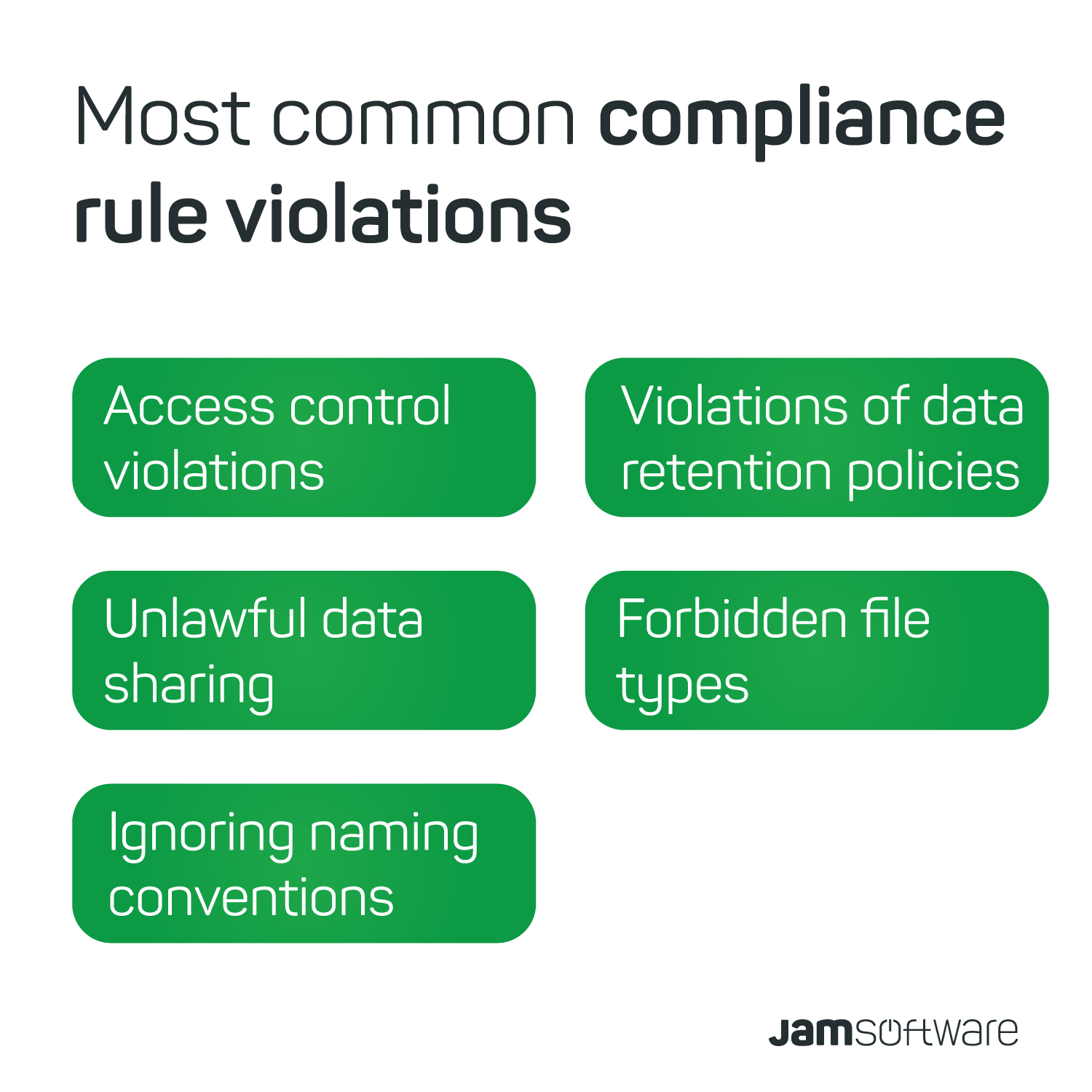
Therefore, it is important to identify some common compliance rule violations. These are:
- Access control violations
- Unlawful data sharing
- Ignoring naming conventions
- Violations of data retention policies
- Forbidden file types
And while these aren’t all types of compliance rule violations, they are some of the most common ones. A more in-depth look at these is advisable.
Access control violations
One critical breach is that access to sensitive data is not secure enough or that the group of people who have access rights is too wide. Employees often retain permission rights long after they change roles and projects. In some cases, even after they have left the company.
A study from Kaspersky from 2022 showed that only around half of the surveyed companies could guarantee that ex-employees couldn’t access company data or corporate accounts.
Regulators have repeatedly fined companies for weak access control uncovered during routine audits, and there are documented cases where ex-employees exploited such oversights to access sensitive information.
Such access control violations almost always originate from a faulty process of role-based access controls (RBAC). Even beyond regulatory consequences companies have a big interest in only allowing certain roles access to certain data.
Unlawful data sharing
The risk does not end with excessive access rights. It also lies in how authorized employees handle company data.
The real danger often starts once data leaves company channels. When files are forwarded to private email accounts, shared via third-party software lacking security or uploaded to unsupported cloud data storage, the potential damage can be immense.
Often it is done for convenience, an employee might want to finish an email at home or finish a work project. Sometimes people share sensitive data with their family or friends without thinking much about it.
But such practices bypass established regulations and open the door not only to serious compliance breaches but also to potential harm to the company.
Auditors and regulators often classify unlawful data sharing as a major compliance rule violation, especially when personal information is shared.
Ignoring naming conventions
An often overlooked compliance rule violation is the ignoring of naming conventions. It seems so trivial, unnecessary and downright bothersome in daily operations. But the consequences are serious. Confusion follows quickly.
There are numerous potential problems:
- Two documents with nearly identical names containing vastly different contents (MarketingData.xlsx versus Marketing-Data.xlsx)
- Multiple files where it is unclear which one is the latest (Final_Report_May.docx versus Report_May_latest)
- During an audit, a specific contract is required but can’t be located in time
- Scripts or automated databases might ignore or misprocess the data
These examples show files without proper naming become difficult to track over time, nearly impossible to locate in an audit and slow down daily operations.
In data management, this undermines the principle of a Single Source of Truth (SSOT), the idea that every piece of information exists in exactly one reliable and authoritative version.
It also ensures that data remains always available and up to date. Most auditors view ignoring of the SSOT in itself as a compliance breach.
Violations of data retention policies
One of the most significant compliance areas concerns data retention. There are numerous regulations that require that certain data must be kept over time not only for taxation or financial purposes but also for data security reasons.
But the violations not only affect the premature deletion of data, they can also occur when data is stored longer than legally allowed. This part of the data life cycle is critical for a lot of regulators.
That is why there are worldwide standards, the most commonly known frameworks are GDPR, HIPAA and SOX.
For example, personal information might be saved over years and never be deleted or employees might have local copies of sensitive personal data outside of compliance regulations.
This data may be impossible to track down and delete in the legally required timeframe.
Not only do regulators repeatedly fine organizations for failing to comply with retention rules, but these violations also almost always result in an irreversible loss of public trust.
The situation becomes even worse if sensitive data is exposed through a data breach. In such cases, the consequences for both fines and public image multiply.
Forbidden File Types
The last of these compliance breaches almost always originates from employees failing to understand the importance of only using company allowed file types.
Some employees download some software that they are familiar with or put personal files like photos or videos on their drives. Not only do such files waste storage resources, but they might also be a security risk.
Malware which is downloaded and hidden in executables or archives, and which might already infest the devices of the employees can now run rampant on company infrastructure.
It becomes even worse if the data is encrypted and can’t be opened.
For auditors the presence of unauthorized files is almost always a red flag. It not only breaches compliance but also undermines data security and company control. Even a few forbidden files can result in hefty fines.
But how can you prevent these compliance rule violations from happening in your company?
The first step is to internalize the risks and establish clear policies that everyone understands.
The second step is to deploy a tool that will help you ensure compliance. We recommend SpaceObServer.
How SpaceObServer helps to enforce compliance
After taking an in-depth look at the challenges IT professionals face when it comes to assuring compliance, we will now take a look at how SpaceObServer can assist with practical tools.
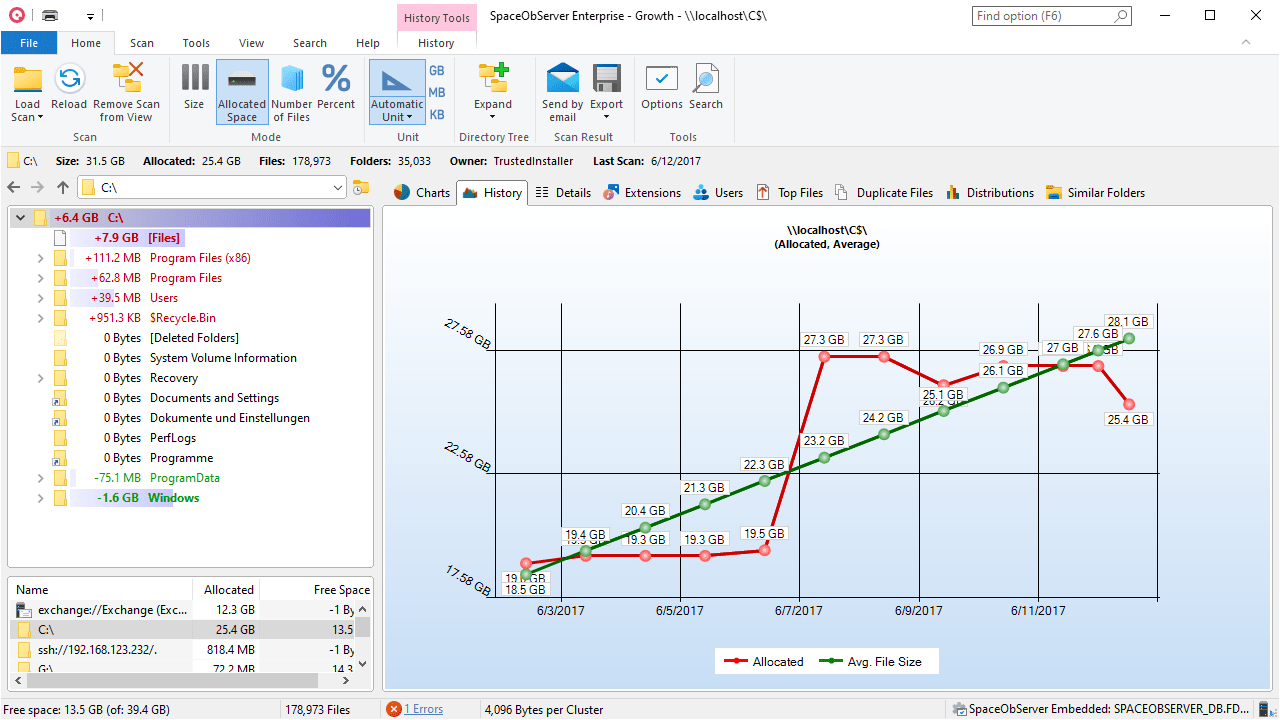
To begin with: SpaceObServer helps IT teams to always gain full visibility over storage capacities down to file level.
Besides that, SpaceObServer also assists in addressing the various compliance risks we discussed earlier. Let’s take a closer look at how it does that.
Address access control violations
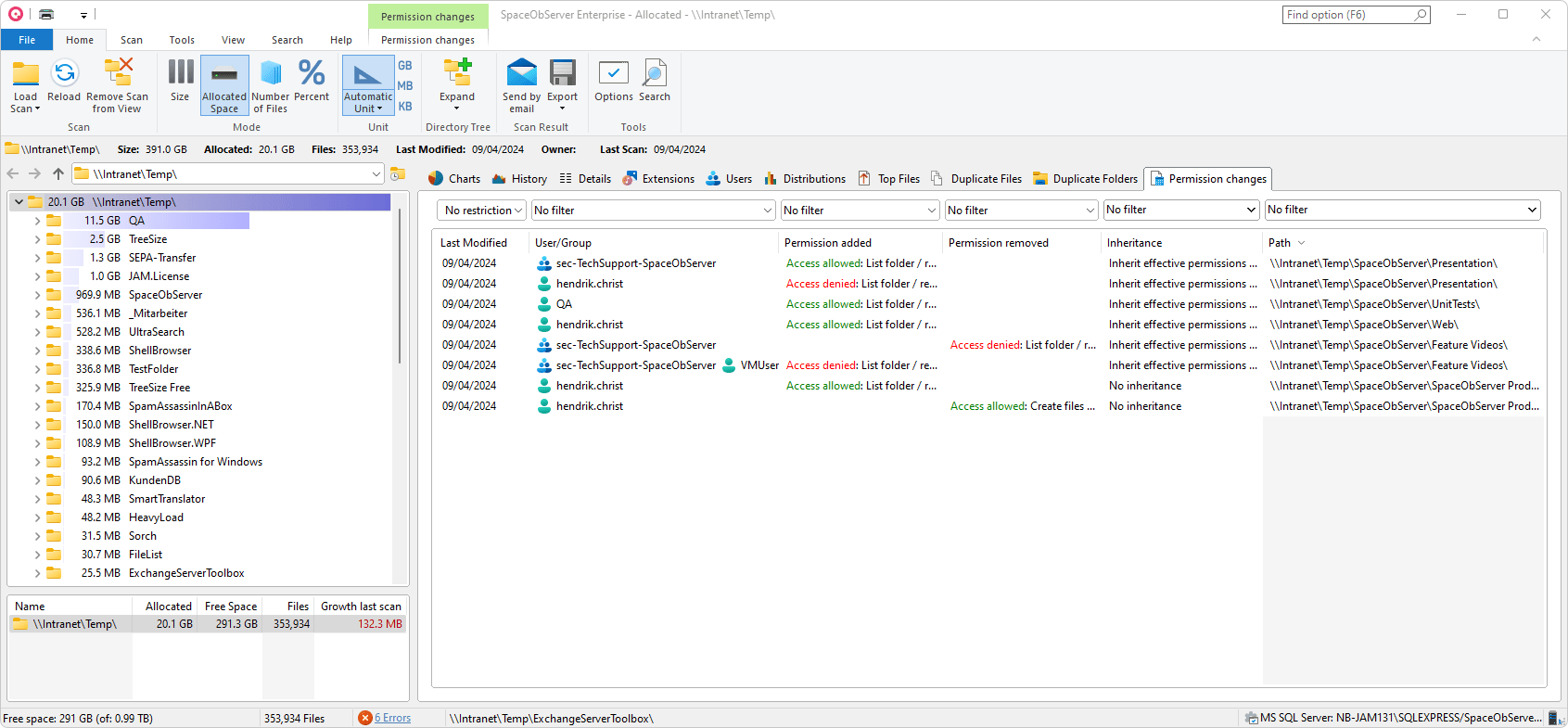
With SpaceObServer, you can quickly analyze access rights and follow permission changes.
SpaceObServer lets you set up regular scans that calculate ACL permission changes. Details such as the modification date, user groups, and inheritance help you better understand the context of a single change and take appropriate action.
Proper access control ensures that you can prohibit the sharing of data without authorization.
Ensure naming conventions
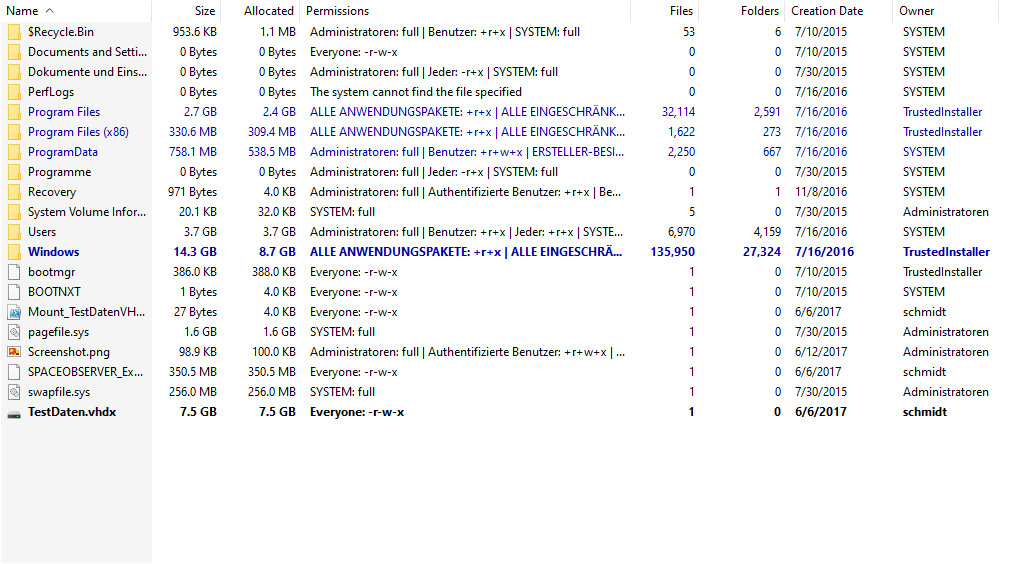
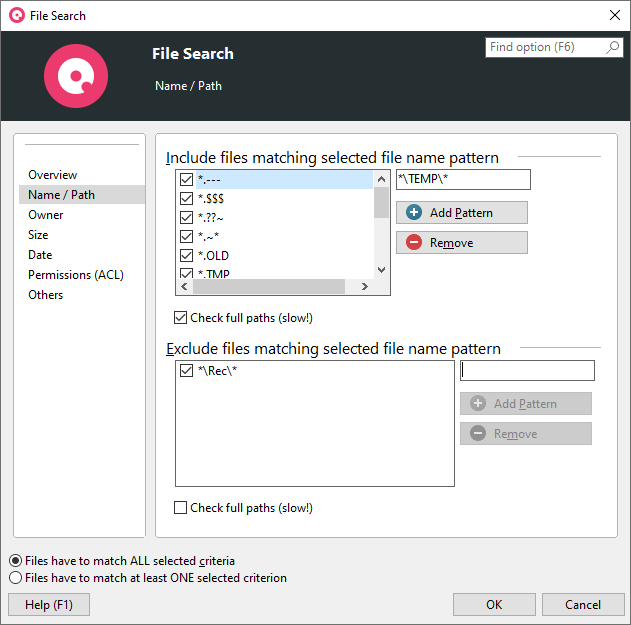
SpaceObServer analyzes file structures and storage patterns. This makes it easy to detect irregularities in naming conventions.
With its integrated file search, SpaceObServer helps you identify recurring naming convention violations. Its bulk renaming feature allows you to correct file and folder names all at once.
Stop violations of data retention policies
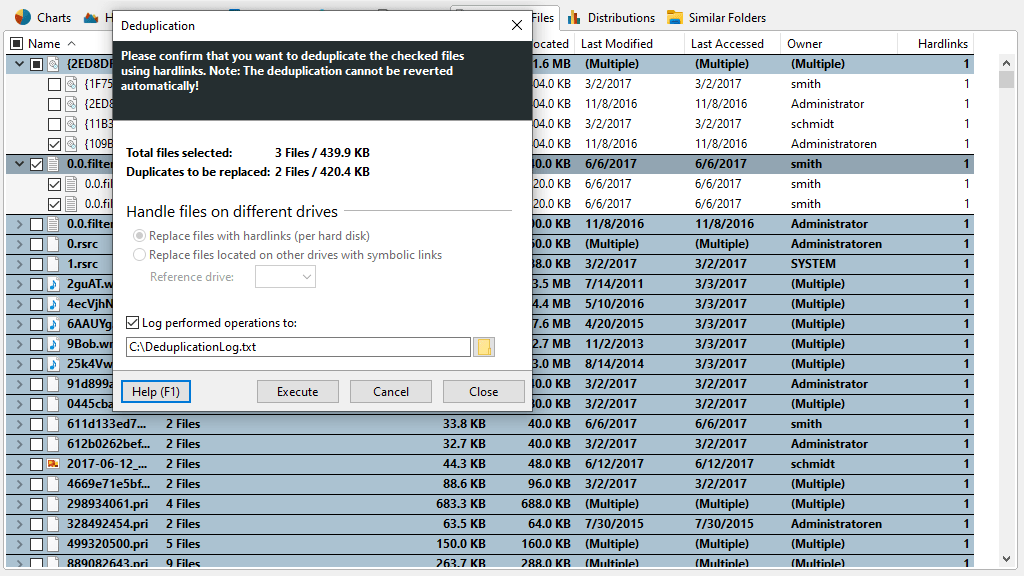
You can use just a few clicks to overlook file duplicates and similar folder structures to ensure data retention policies.
During every storage scan, SpaceObServer calculates checksums to identify duplicate files throughout your entire storage landscape. In a dedicated tab, you can compare metadata and act, such as deleting the files immediately.
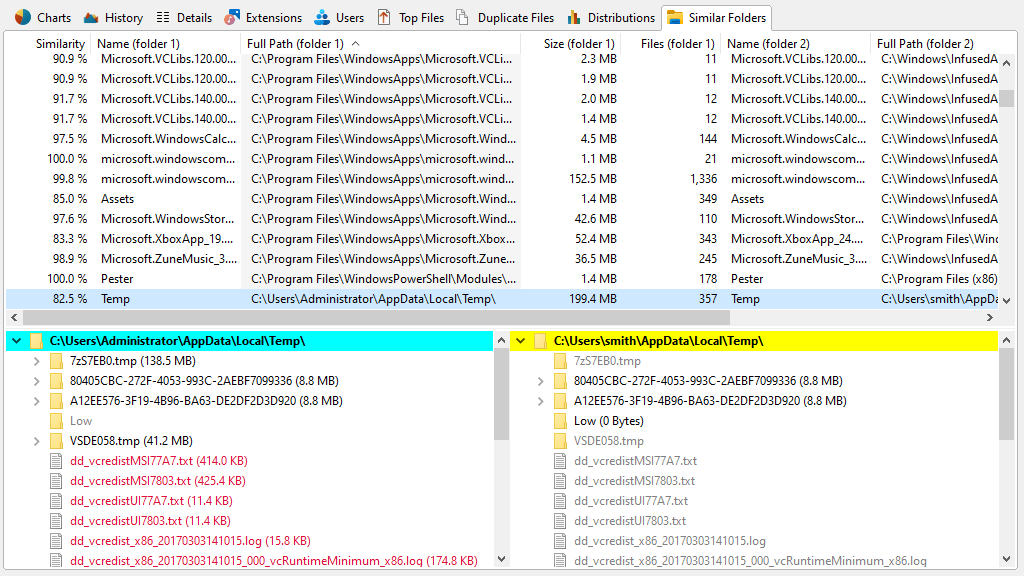
Besides exact duplicates, SpaceObServer also detects similar folder structures that you can analyze interactively.
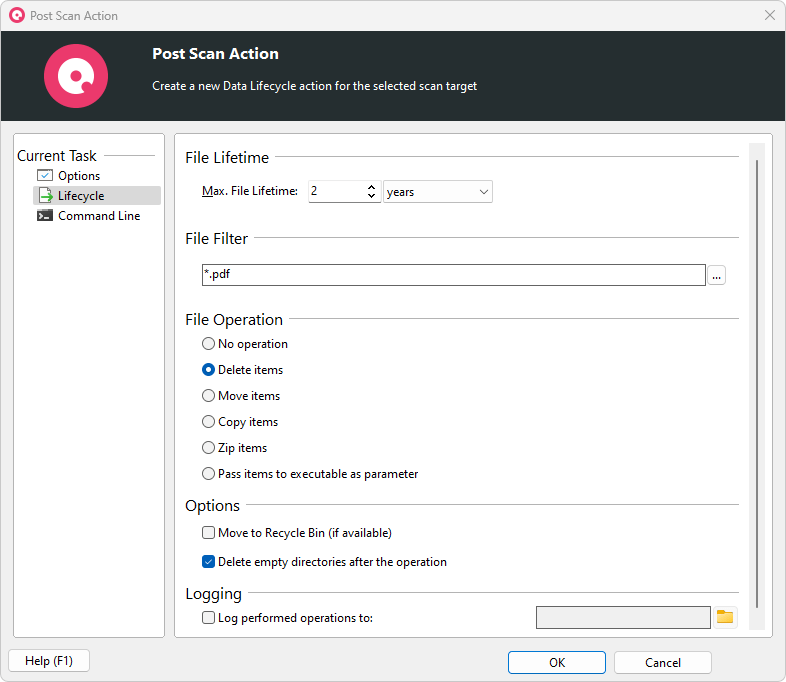
No more forbidden file types
With SpaceObServer, you can perform file operations based on data types and file extensions across your different storage systems.
Filter out forbidden file types and take ad-hoc action on demand.
To ensure that file type rules are met in the long term, you can set up automatic data processing to regularly move or delete prohibited file types, such as on a monthly schedule.
Start your free SpaceObServer trial today
SpaceObServer is a powerful storage management solution containing a variety of tools that ensure compliance, oversee storage losses, and clean up and report.
Try SpaceObServer yourself and start your free trial today.
Feel free to contact us if you have any questions left. We are happy to help!